CyberLock’s Wireless Access Control Solution
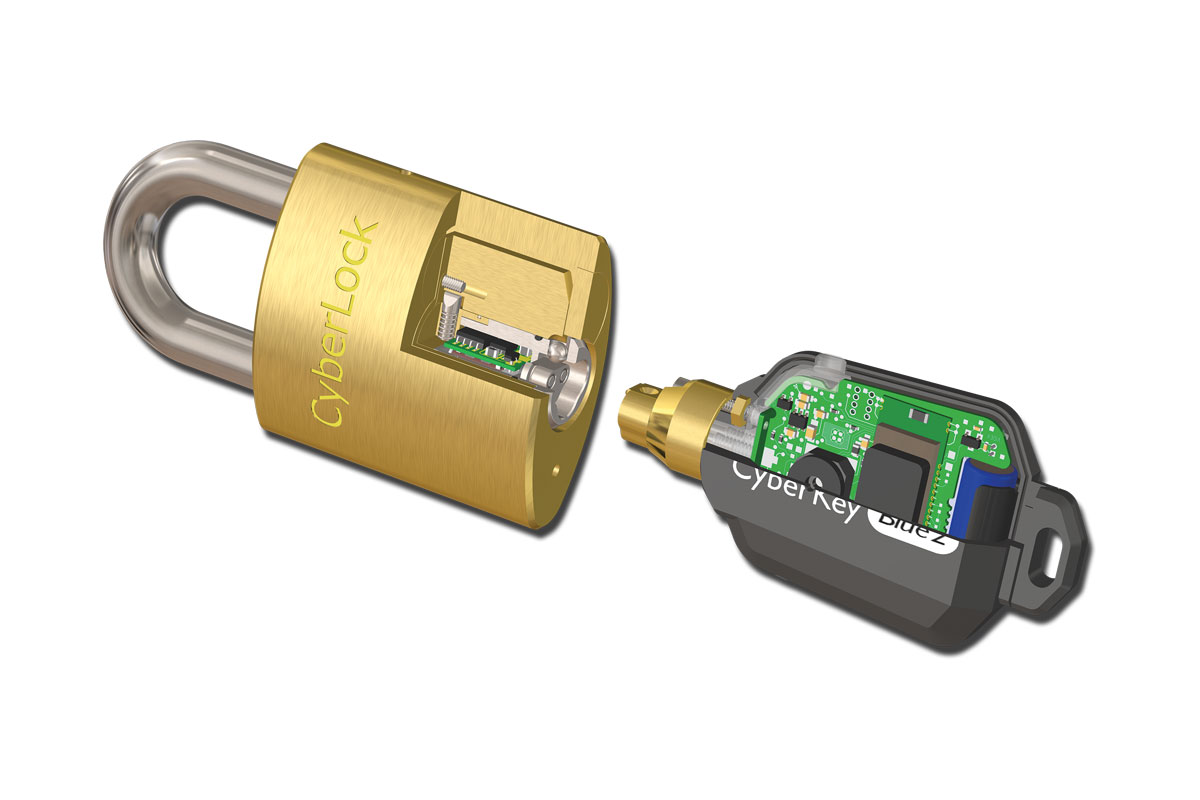
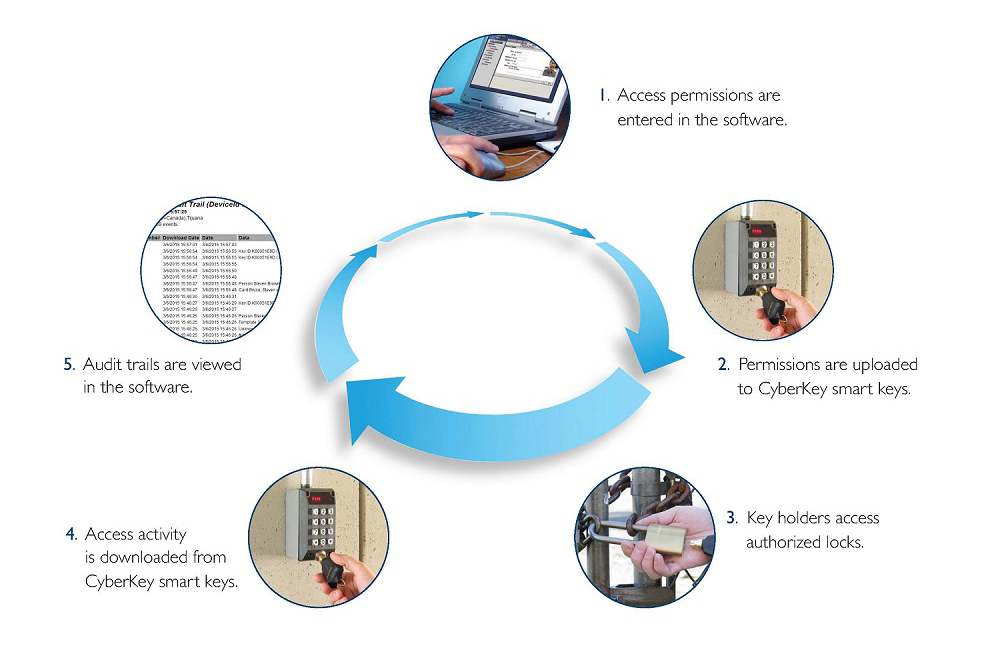
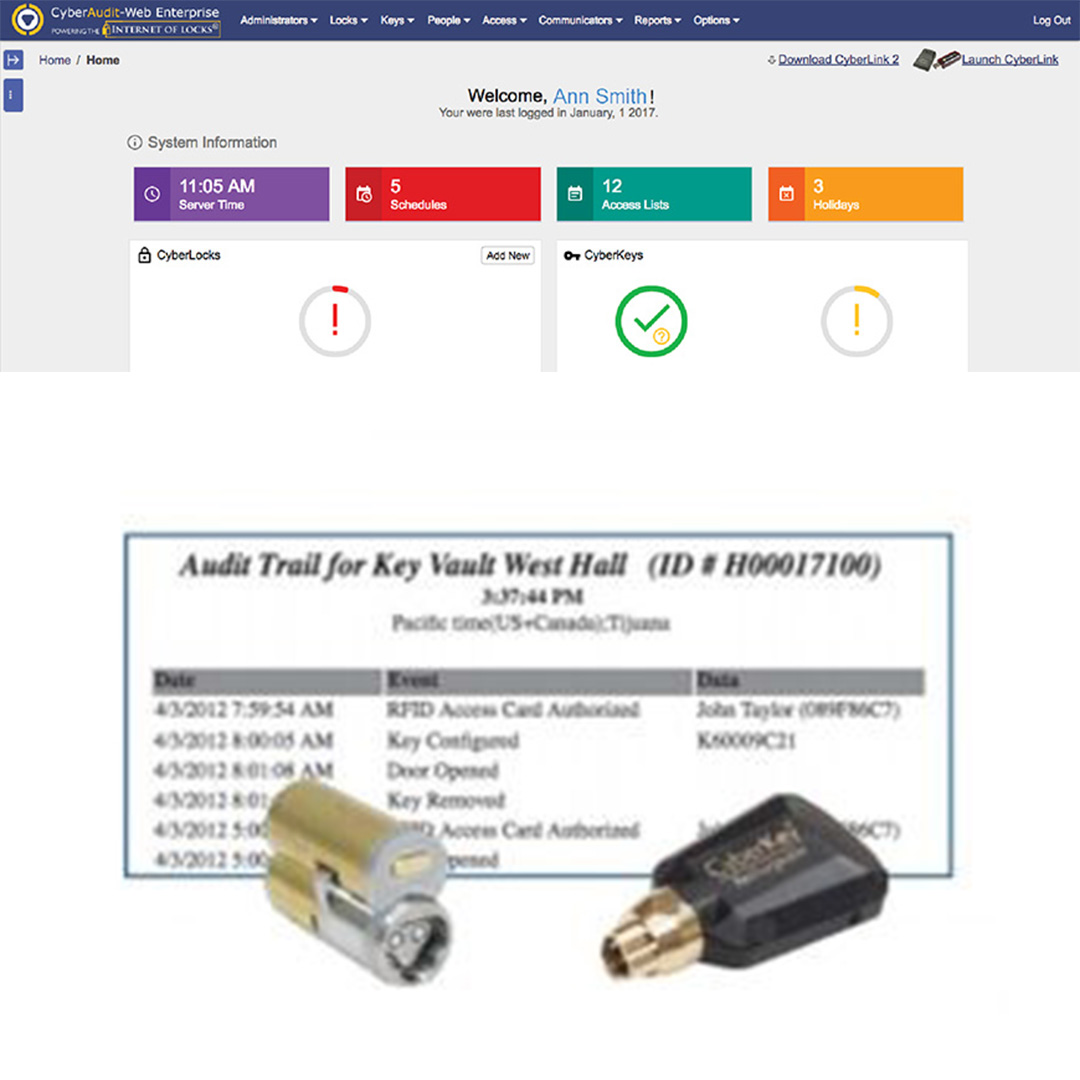
CyberLock is the world’s first key-centric wireless access control system. You are now able to control and track access to every locking point in a facility, without running wire! Receive audit trails and access reports on personnel to increase accountability. Secure almost anything with over 400 different lock options. Set permissions and schedules for each key holder to restrict access. Disable lost or stolen keys to reduce the risk of a security breach. With CyberLock, organizations are able to increase security, accountability, and key control.
- Versatile – With no wiring or power needed to operate, CyberLock’s wireless access control cylinders can be used to secure doors, padlocks, cabinets, gates, vehicles, lock boxes, and more.
- Scalable – Since it is a completely wireless access control system, you can grow the system over time without having to disrupt infrastructure.
- Cost Effective – System is installed without power or wiring so you no longer have to spend money on wiring and conduit.
- Convenient – With user-friendly cloud based software, making updates to the system is seamless and can be done from anywhere.